“Customer data is more important to Salesforce than anything else!”
The customers trust Salesforce for their data. All the customer data is present on the Salesforce cloud, making cloud security very important for both the customers & the company.
So, what is AppExchange & why AppExchange security is essential to Salesforce?
AppExchange is an ecosystem of different types of partners who have applications.
When partners are putting up applications on AppExchange, which will be installed by customers, this is where customer sensitive data is residing. It is crucial to make sure that these applications are secure.
When customers have to buy something & they understand that the product is secure to buy, they don’t need security engineers to check the applications.
READ: AppExchange App Development Best Practices
So, the question here is, how does Salesforce secure the AppExchange ecosystem?
A written application has to go through the process of security review.
There are different layers of protection to secure the AppExchange ecosystem.
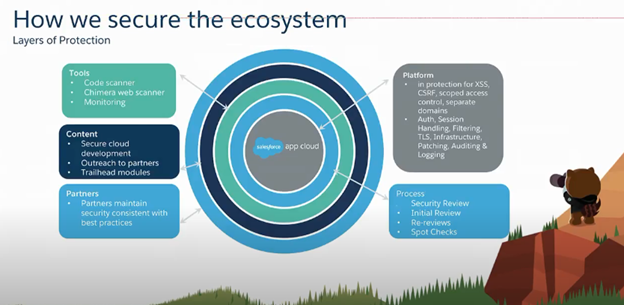
*source: salesforce
RECOMMENDED: How to Ensure Business Success on AppExchange?
TOOLS:
Code Scanner: Used to scan the code.
Chimera Web Scanner: To run any application outside the ecosystem, so that APIs are secure
Monitoring services.
CONTENT:
There is a vast amount of published content for the past many years on Salesforce. There is an entire developer web page where Salesforce has everything on security. Also, there are a bunch of trailhead modules talking about the security review process.
Like how to do secure coding, the partner developers are highly confident about submitting for review and code secure the link.
PARTNERS:
Partners are building applications. It is a shared responsibility between Salesforce & the partners to maintain the ecosystem & keep its security.
THE TEAM IN THE SECURITY REVIEW PROCESS
ISV PARTNER TEAM:
ISV partner account manager: They are the primary source of contact.
ISV Technical Evangelist: Helps partner prepare for security review.
Security review operations: Review the partner’s submissions and responsible for notifications to partners.
PRODUCT SECURITY TEAM:
This team has a product security engineer that provides guidance and reviews applications. They are manually observing the code and making sure that everything is fine.
PRODUCT DEVELOPMENT OUTSOURCER:
This team is developing for partners for the AppExchange ecosystem. They help assist in security review success.
ALSO READ: 5 Must Things To Consider While Outsourcing AppExchange App Development
TESTING IN THE SECURITY REVIEW PROCESS
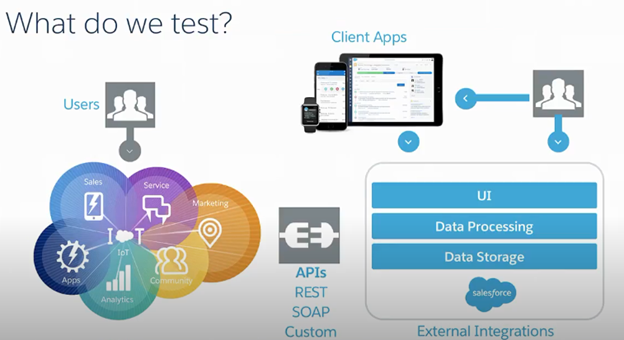
*source: salesforce
The main question in a security review process is what exactly happens during the process.
Let’s study the whole ecosystem in the above image.
Users connect to different departments of Salesforce like Sales, Marketing, Apps, Analytics, etc.
Salesforce is also externally connected by APIs and has external integrations for data processing and storage.
The Salesforce data is accessible on the cloud through different external client apps.
So every minute flow of Salesforce starting from users, external APIs & accessible client apps that are accessing Salesforce data are tested. It starts with touching and impacting the Salesforce data.
Any vulnerability in the whole flow puts Salesforce data at risk. That’s the reason full-scope testing is necessary.
SECURITY REVIEW PROCESS
*source: salesforce
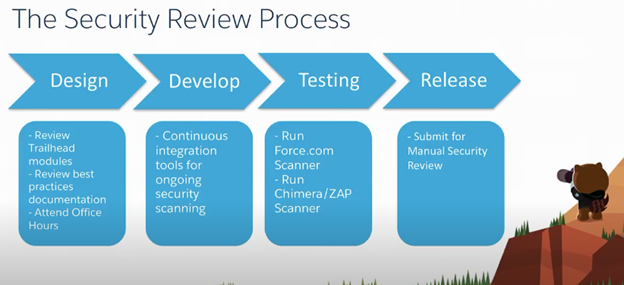
Salesforce accelerates the security review process in four easy steps:
DESIGN: In design, one has to go and review trailhead modules. It has a lot of secure coding content.
Submission process office hours: One can ask process-related questions accessible at https://sfdc.co/submissionofficehours
Security review technical office hours: Customers can book office hours with Salesforce.com for discussion on different topics, details of which are available at https://sfdc.co/securityofficehours
DEVELOP: Start writing the code. Do testing of written code, if it is working as intended.
This stage focuses on developing tools for security scanning.
TESTING: This phase makes use of tools like:
Force.com source scanner helps find common security issues in native code. It also includes a manual code review for adherence to secure coding guidelines.
Zap scanner finds common web vulnerabilities.
Chimera Scanner is a fire & forget cloud scanner that runs ZAP as an engine.
RELEASE: This is the final step to submit for manual security issues.
5 Reasons to Build your AppExchange Solution with a Product Development Outsourcer (PDO)
Let’s Conclude:
The AppExchange security review process helps secure the Salesforce ecosystem starting from design to release. Secure AppExchange means less vulnerability to security threats and a more robust Salesforce platform.
CEPTES is a Salesforce Silver consulting & Product Development Outsourcer partner that can guide you as your strategic partner to speed up the business value of your Salesforce.com investment through app development. consultation, digitization, and innovation. If you are thinking of growing your business using the Salesforce platform, then get in touch; we are happy to help you.